
The essential guide to DMARC policies for marketers and email developers
Email spoofing, phishing scams, and other cybercrimes are more prevalent than ever before. That’s why email authentication has become an increasingly important aspect of email marketing and communication. The Domain-based Message Authentication, Reporting, and Conformance (DMARC) protocol is one of the most widely used methods for verifying the authenticity of emails. And guess what? Google and Yahoo now expect bulk email senders to have a DMARC policy.
This guide will help you understand the importance of DMARC and how to set it up. Whether you’re a seasoned email marketer or just getting started, understanding DMARC will be beneficial for ensuring your emails reach your recipients’ inboxes.
Let’s jump in!
Which DNS records relate to deliverability?
Domain-level SPF, DKIM, and DMARC records help ensure your emails reach their intended recipients by letting inbox providers know that you are who you say you are. They serve as a digital signature of sorts, proving that the sender truly owns the sending domain.
Three types of DNS records impact deliverability:
- SPF (Sender Policy Framework): This record verifies which IP addresses can send emails with your domain.
- DKIM (DomainKeys Identified Mail): This record adds a digital signature to your emails, guaranteeing their authenticity and ensuring that the messages you send are identical to the ones that arrive in the inbox.
- DMARC (Domain-based Message Authentication, Reporting, and Conformance): This record extends SPF and DKIM, offering guidance on how to handle emails that fail authentication checks.
Ensuring these records are in place and configured correctly is crucial to maintaining a high deliverability rate and reducing the chances of misusing your domain for fraudulent activities. If you’re sending emails from the Customer.io network, we require you to create SPF and DKIM records, and we strongly encourage implementing a DMARC policy.
Why is DMARC important?
DMARC has become increasingly essential in protecting both businesses and consumers from bad actors sending emails on behalf of their respective sending domains. At its core, a DMARC policy instructs inbox providers on what to do if they receive an unauthenticated email from your domains.
How to set up and monitor your DMARC policy
Your DMARC policy is set up in your domain name registrar. The person in your organization responsible for managing the DNS records of your sending domains will need to create your DMARC policy’s TXT record.
To satisfy Gmail and Yahoo’s requirements, you must create the minimum DMARC record: “v=DMARC1; p=none“
This record says, “We have a DMARC policy, but no further instructions are given when SPF/DKIM are not aligned.”
If you are unsure if your domain currently has a DMARC policy in place, you can quickly look that up using an online tool. MXToolbox’s DMARC Check Tool is one of many options available. If your domain is configured in Customer.io, we will also let you know if you have a DMARC policy that covers a given domain:
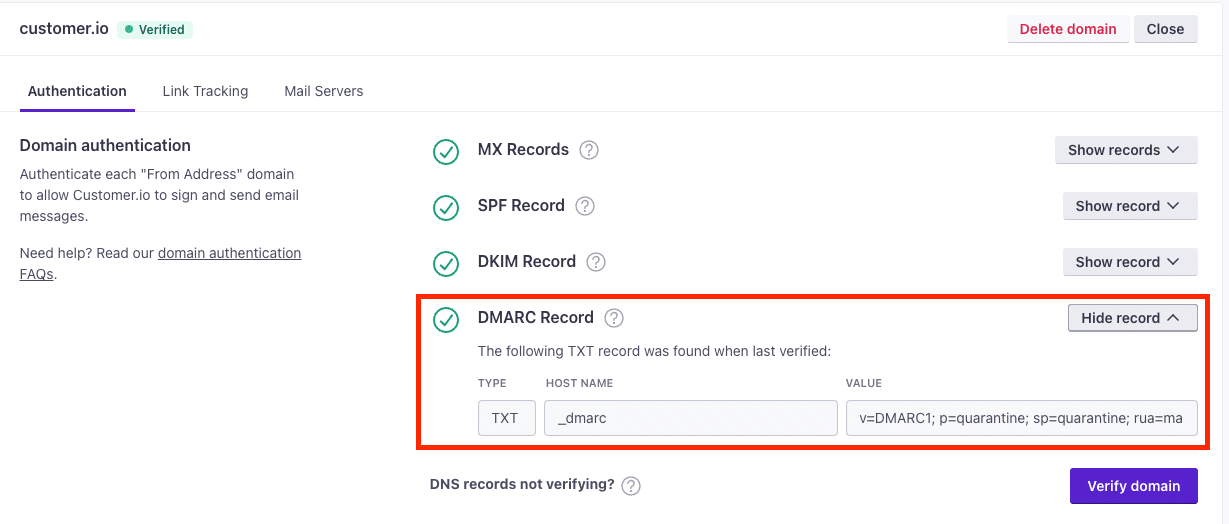
To set it up is easy. Navigate to your domain name registrar’s DNS configuration and create this record:
- Type: TXT
- Host: _dmarc.mydomain.com (replace mydomain.com come with your root domain)
- Value: “v=DMARC1; p=none“
Important note: This policy is the bare minimum configuration. For those who wish to expand this configuration, get information on DMARC policies. A DMARC policy on your root domain will impact all email sent from this domain (including any subdomains).
For this reason, start with the none policy to monitor the impact on your legitimate email traffic. Then, gradually enforce stricter policies like quarantine or reject as you gain confidence in your email authentication setup at Customer.io and any other email-sending providers you use.
DMARC monitoring
After implementing DMARC, you can regularly monitor the reports sent to the email addresses specified in the rua and ruf tags. These reports will provide insights into the sources of email traffic using your domain and help you refine your email authentication settings. All that is needed to receive these reports is to include an email address to send your daily reports to:
v=DMARC1; p=none; rua=report@mydomain.com; ruf=report@mydomain.com
rua: Aggregate reports email address.
ruf: Forensic reports email address.
Aggregate reports provide high-level statistical data about email traffic sent from your domain, while forensic reports provide detailed information about individual emails that fail DMARC authentication.
These reports are sent daily to your policy’s specified email address in the form of an XML file. With that said, the most common means of consuming and viewing the data generated from these reports is via a DMARC monitoring platform. There are a number of these platforms, and a simple Google search will help you find one that works for you.
A robust DMARC policy is non-negotiable
Email authenticity can significantly impact your business’ reputation. By carefully setting up and monitoring your DMARC policy, you not only adhere to the requirements set by Google and Yahoo, but you also gain valuable insights into the health and deliverability of your email campaigns.
Remember, a well-maintained DMARC policy adds credibility to your emails and ensures they reach their intended recipient’s inbox. That’s great for you—and your customers.
If you want to learn more about email deliverability, sign up for our 5-part email series. You’ll learn everything you need to know to become a deliverability expert.